All the wireless networks are encrypted using WEP or WPA/WPA2 keys. To hack into a wireless network you need to find the security key. The following tutorial will deal with cracking the WPA/WPA2 security key. This tutorial is only for educational purpose, I'm not responsible for your bad deeds.
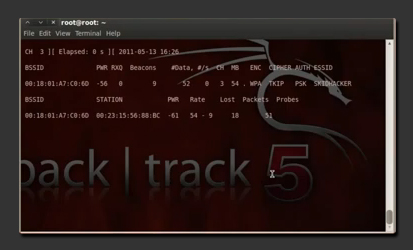
 What is needed to crack a WPA or WPA2 key is something called a WPA Handshake. You can obtain a handshake by kicking someone off the network, and those computers will automatically reconnect which will give you the handshake. This means, if there is no one on the network, you can't get a handshake, and you can't crack the WPA network. So how do we know if someone is connected? Well look at the lower part of the airodump command, and you will notice something as STATION, and underneath that if someone is connected it wil show you their mac address.
What is needed to crack a WPA or WPA2 key is something called a WPA Handshake. You can obtain a handshake by kicking someone off the network, and those computers will automatically reconnect which will give you the handshake. This means, if there is no one on the network, you can't get a handshake, and you can't crack the WPA network. So how do we know if someone is connected? Well look at the lower part of the airodump command, and you will notice something as STATION, and underneath that if someone is connected it wil show you their mac address.
More Tutorials on hacking Wireless Networks:
Hacking WEP Wireless Network using backtrack.
Hacking WEP Wireless Network using FERN WIFI Cracker(GUI).
Hacking WEP Wireless Netwok Without Using Dictionary.
Hacking WEP Wireless Network using backtrack.
Hacking WEP Wireless Network using FERN WIFI Cracker(GUI).
Hacking WEP Wireless Netwok Without Using Dictionary.
For this tutorial you need WPA/WPA2 wordlist, which can be easily found on torrent (bigger the wordlist, more are the chances of cracking the passwords)
backtrack 5 GNOME or previous versions (which can be easily downloaded from its official site) and a compatible wireless card that supports packet injection.
Install backtrack on your computer using dual boot or normal method (I'm not going deep into the installing part as I guess you can figure it out on your own)
At the startup you can use"startx" for backtrack's Graphical User Interface (GUI)
If you are asked for username and password use this:
Username: root
Password: toor
Follow these steps carefully to successfully Hack into WPA/WPA2 Wireless Network:
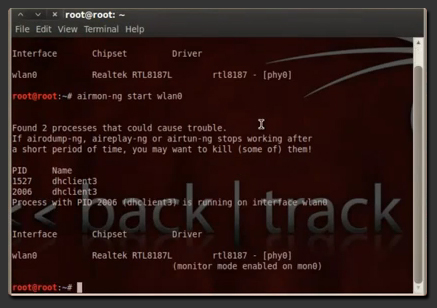
Okay, so firstly open up a terminal and once we have the terminal open we are going to type in airmon-ng which will display our wireless interfaces. In my case I have wlan0, and now we are going to put it into monitor mode. To do that, type airmon-ng start wlan0. As you can see on the picture below it says (monitor mode enabled on mon0), and we are going to be using mon0 instead of wlan0 as our interface.

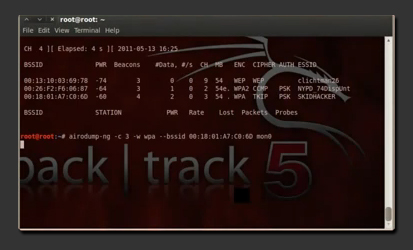
Lets type in airodump-ng mon0 and this command is going to initiate the scanning process for Wi-Fi networks. As you can see in the picture below, a few WPA encrypted networks should pop up. I'm going to attempt to crack the network under the essid SKIDHАCKER. Take a note of the channel, and you want to copy the BSSID for later use.
Now we are going to type in airodump-ng -c (channel) -w (filename) --bssid (bssid) mon0, and replace the values to fit what you got from the last step. Don't forget to remember what filename you chose, because we are going to need that at the end.
 What is needed to crack a WPA or WPA2 key is something called a WPA Handshake. You can obtain a handshake by kicking someone off the network, and those computers will automatically reconnect which will give you the handshake. This means, if there is no one on the network, you can't get a handshake, and you can't crack the WPA network. So how do we know if someone is connected? Well look at the lower part of the airodump command, and you will notice something as STATION, and underneath that if someone is connected it wil show you their mac address.
What is needed to crack a WPA or WPA2 key is something called a WPA Handshake. You can obtain a handshake by kicking someone off the network, and those computers will automatically reconnect which will give you the handshake. This means, if there is no one on the network, you can't get a handshake, and you can't crack the WPA network. So how do we know if someone is connected? Well look at the lower part of the airodump command, and you will notice something as STATION, and underneath that if someone is connected it wil show you their mac address.
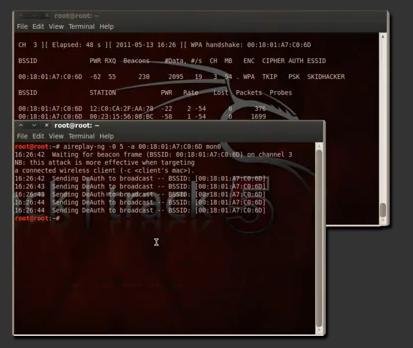
Once you get a handshake, airodump will alert you in the top screen, and the handshake will be located right from the time stamp. Okay, so lets open up a new terminal and we are going to kick off the computers connected. Lets type in aireplay-ng -1 0 -a (bssid) mon0. replace bssid with the network you are trying to crack and hit enter. It is going to attempt to kick off a client, and if it succeeds you will see the wpa handshake at the top right corner, if you don't run the aireplay command a couple of times.

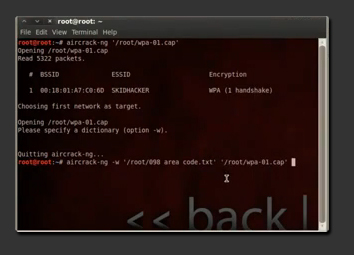
So now that we have a wpa handshake file, we are going to attempt to crack it. Lets stop the scan by pressing CONTROL + C on the terminal where airodump is running. Now in order to find the handshake file, you need to go in the top menu and chose Places > Home Folder. Okay, so lets open up a terminal and we are going to type in aircrack-ng -w (dictionary) /root/(filename). Where filename is the filename you specified when capturing the wpa handshake and the dictionary is the path of the wordlist you downloaded. This can be done by dragging in the handshake file into the terminal after the aircrack-ng -w (dictionary) command and it will parse in it's directory. All you need to do is hit enter. The password needs to be in the dictionary file, so the bigger the wordlist is the bigger are the chances of you getting the password.

If the password is in the wordlist, it will give you a success message.




airmon-ng doesn't shows anything..
ReplyDeleteThat means your wireless card is not supported.. You may use any other external wireless card(a supported one) that are easily available on ebay.
ReplyDeletenicely explained, and it works as now I'm using my neighbours connection. Is it against the law?
ReplyDeleteIt depends upon the country you reside in.
ReplyDeletei am trying to crack wpa/wep wireless network .The following message was displayed .
ReplyDeletearjun@arjun-HP-Pavilion-g6-Notebook-PC:~$ ls -l | grep mac
-rw-r--r-- 1 root root 38565 2012-02-18 08:53 mac-01.cap
-rw-r--r-- 1 root root 378 2012-02-18 08:53 mac-01.csv
-rw-r--r-- 1 root root 580 2012-02-18 08:53 mac-01.kismet.csv
-rw-r--r-- 1 root root 1590 2012-02-18 08:53 mac-01.kismet.netxml
arjun@arjun-HP-Pavilion-g6-Notebook-PC:~$ aircrack-ng mac*.cap
Opening mac-01.cap
Read 672 packets.
# BSSID ESSID Encryption
1 00:E0:4C:02:77:28 ANTHB No data - WEP or WPA
Choosing first network as target.
Opening mac-01.cap
Got no data packets from target network!
Quitting aircrack-ng...
.
Anybody help me how to crack wpa/wep wireless network
This tutorial is for cracking wpa wireless network.
ReplyDeleteFirst make sure which network are you trying to crack WPA or WEP?
Tutorial for cracking WEP is given here:
http://www.ubertechblog.com/2011/08/hacking-wep-wireless-network.html
And if you find it complicated, use this link that explains the same using GUI:
http://www.ubertechblog.com/2011/08/hacking-wep-wireless-network-using-fern.html
please give me the link which i can download wordlist file directiotn without turrnet
ReplyDeletethe size of the file for wordlist is like 3-20GB, it's not possible to find such a wordlist any file sharing site. Torrent is the only option.
ReplyDeleteWhy did you wrote
ReplyDeleteaireplay-ng -1 0 -a (bssid) mon0
but in the image is
aireplay-ng -0 5 -a (bssid) mon0
Which is the difference?
when i type airodump-ng mono0 i get this message "failed: No such device" is there anything am not doing right. Help!!
ReplyDeleteThe 0 and the 5 are the number of times you want the command to be ran.
ReplyDeleteI am facing a problem while trying to hack WPA2
ReplyDeleteWhen I run the command aireplay-ng -1 0 -a __bssid mon0
it shows association denied (code 40)
Please help
diference is that in aireplay-ng -1 0 -a (bssid) command machine try to deauth. with large attemtp, they not stop until ctrl+c command is given and in secound command aireplay-ng -1 5 -a (bssid) number 5 is number of atempt for deaut. So just 5 times.
ReplyDelete
ReplyDeleteSometimes it is difficult to manage airodump-ng output files. i mean once i generate those csv and xml files then after i start looking into it so for large amount of data i can't figure it out. so is there any tools or services available for analysis and visualization ? i have used this website and it is quite
good, here i have shared my sample data have a look and also share any other sources if anyone knows. - http://bit.ly/1Nbfgm6
I
ReplyDeleteHi guys....I got no data packets from Target network problem....what I do...any solution for this problem....plz any one help me guys......
with all instructions are still the same problem
ReplyDeletegot no data packets from target network
got no data packets from target network
got no data packets from target network